Topologies
Compare physical topology with logical topology.
- Physical topology refers to the actual architecture of a network, how the wires and nodes are connected in space.
- Logical topology refers to the flow of data packets within a network's wires and nodes(a network with a start topology, may behave as a bus network).
Define physical star network topology.
each client has its own private connection to the central hubthe hub receives packets for all the clients connected to it and redirects it to the intended recipient
Define physical bus network topology.
There is a single cable called the backbone2 devices each on the end of the backbone called terminators.
State 4 advantages of a physical star topology.
- Greater security, packets are only sent to intended recipient, other clients cannot see the data packets of other clients transmissions
- Collisions cannot occur as each client has its own private connection to the central hub
- Easy to add and remove clients from the network
- The failure of a single cable does not affect the performance of the whole network
State 2 disadvantages of a physical star topology.
- The central hub is a single point of failure.
- More cabling required so more expensive to install.
State 1 advantage of a physical bus network topology.
Inexpensive as a minimum length of cabling is required to install.
State 3 disadvantages of a physical bus network topology.
- Lower security as each client can see every packet traveling on the backbone, regardless of whether they were the intended recipient.
- Greater likelihood of collisions as each client may not be synchronised with every other client (affects performance).
- Backbone is a single point of failure.
Network Types
Define client-server network.
- One machine is nominated as the server.
- They are many client machines.
- The server machine provide files and serves on request of the client machines.
Define peer-to-peer networks.
Each device on the network has equal status, it can behave both as a client and a server.
State 3 advantages of client-server networking.
- The resources of a more powerful machine may be made available to larger number of less powerful machines.
- Data on a client-server network is centralised, so backup is centralised and thus easier.
- Data on the client-server network is centralised, so centralised management of access rights and file permissions and limits may be enforced easily (greater security).
State 3 disadvantages of client-server networking
- More expensive.
- Difficult to set up and maintain.
- Individuals with a high degree of expertise may need to hired in order for central management.
State 4 advantages of peer-to-peer networking
- More cost effective.
- Easier to set up and maintain.
- No one machine needs to be particularly more powerful to provide all the services to each client.
- If one machine malfunctions only the services it provides become unavailable, compared to all services.
State one disadvantage of peer-to-peer networking.
All the clients which provide services must be functional in order for the network to be fully operational.
Wireless Communication
Define WIFI.
An implementation of a wireless local area network, based upon international standards, used to enable devices to connect to a network wirelessly.
Define WAP.
A device connected to the central hub which broadcasts and receives radio signals which have encoded data packets to devices with network interface cards.
Define NICs.
A device used to receive, decode and translate radio signals containing data packets.
Explain why a wireless network is seen as less secure than a wireless network.
Data packets are broadcast over a general areaAny NIC within the range can intercept data packets.
State 3 methods which when implemented make a network more secure.
WPA/2 encryption -> Disable SSID broadcast -> MAC address filtering
Explain how WPA makes a network more secure.
Encrypts all data packets broadcast, required a password to decrypt. Only those devices with password can understand data packets broadcast.
Explain how disabling SSID broadcast makes a network more secure.
A SSID identifies a WAP. Disabling SSID broadcast, means the network is not shown in the list of available network produced by computersOnly those who know a wireless network exists and its SSID can attempt to connect to it.
Explain how MAC address filtering makes a network more secure.
- Each NIC has a MAC address which uniquely identifies it.
- Each request sent to the WAP includes this information.
- By creating a whitelist, only those approved devices can successfully connect.
- By creating a blacklist, known individuals can be prevented from accessing the network.
What does WPA stand for.
Wireless Protected Access.
What does SSID stand for.
Service Set Identifier.
What does MAC address stand for.
Media Access Control.
State the protocol used to avoid collisions within a small wireless network.
CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance).
Explain why CSMA/ CA alone is not sufficient to avoid collisions within a large wireless network.
Hidden nodes, where a device checking an idle channel is blocked from seeing some other nodes, and thus views an channel as idle, when the other node is communicating.
State the protocol implemented on top of CSMA/CA in order to solve the problem of hidden nodes.
RTS/ CTS (Request To Send/ Clear To Send).
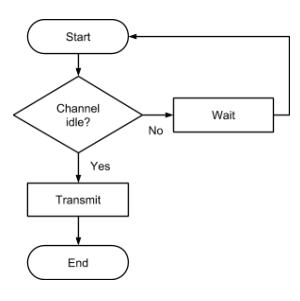
Describe the CSMA/ CA protocol.
- A transmitting device checks to see if the channel is idle.
- If the channel is idle, then transmission begins.
- If the channel is busy then an exponential back-off algorithm is used to wait a random, increasing period of time before checking the channel again.
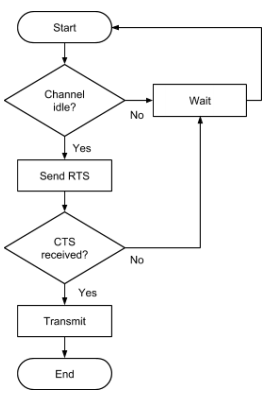
Describe the CSMA/ CA protocol with RTS/ CTS
- A transmitting device checks to see if the channel is idle.
- If the channel is busy then an exponential back-off algorithm is used to wait a random, increasing period of time before checking the channel again.
- If the channel is idle, then a request to send signal is transmitted.
- The transmitting device waits for a clear to send signal for a set period of time.
- If a CTS received then transmission begins.
- If a CTS is not received with in a period of time, the device will use a exponential back off algorithm to wait a random, increasing period of time, before checking of the channel is idle again.